Part 7 - Hacking char
Today we hack the simple char program.
Let's review our code.
#include <stdio.h>
#include "pico/stdlib.h"
int main()
{
stdio_init_all();
while(1)
{
char x = 'x';
printf("%c\n", x);
sleep_ms(1000);
}
return 0;
}
Let's fire up our debugger.
radare2 -w arm -b 16 0x03_char.elf
Let's auto analyze.
aaaa
Let's seek to main.
s main
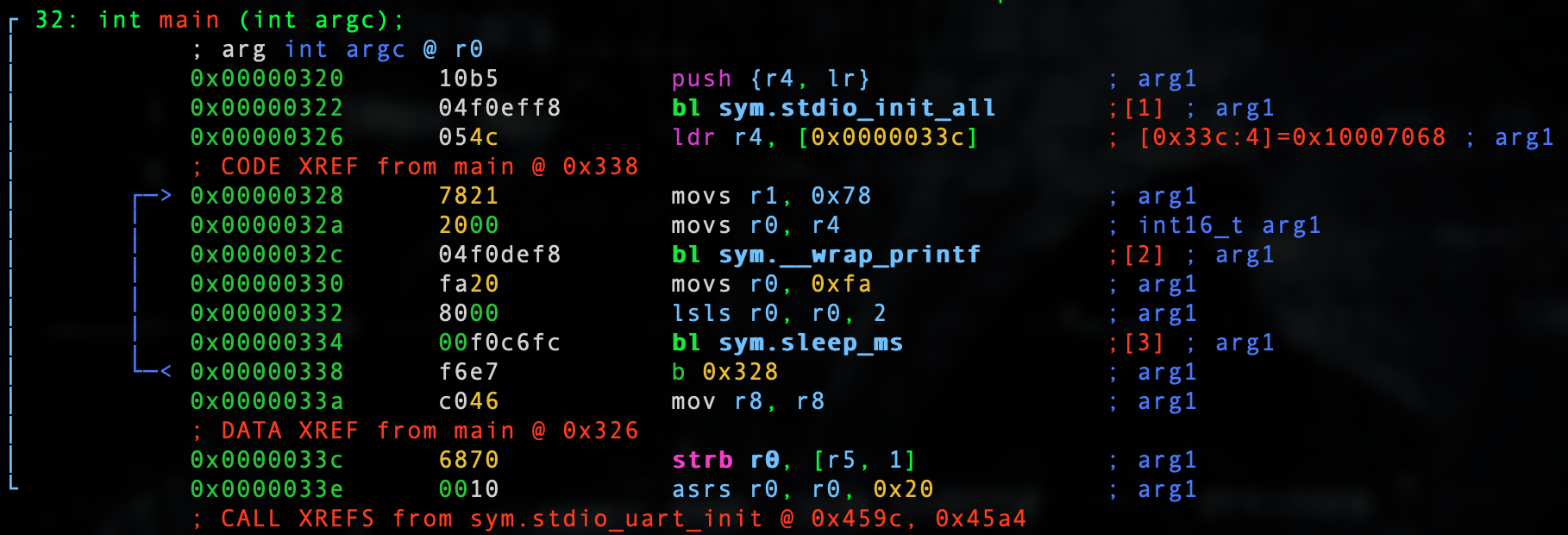
Let's go into visual mode by typing V and then p twice to get to a good debugger view.
In our last lesson we broke down each line. Here we are clearly interested in hacking the value of 0x78 and changing that to anything we want. Let's try 0x79. This simple hack will turn the char 'x' into 'y'.
:> wa movs r1, 0x79 @ 0x00000328 Written 2 byte(s) (movs r1, 0x79) = wx 7921
Let's verify the change.
:> pd 1 @ 0x00000328 │ ; CODE XREF from main @ 0x338 │ 0x00000328 7921 movs r1, 0x79 ; 'y' ; arg1
In this case our debugger is even telling us it is in fact 'y' in addition to now we are moving the hex ascii value into 0x79 into r1.
Let's also hack the sleep time to 2000 ms or 2 seconds.
:> wa lsls r0, r0, 3 @ 0x00000332 Written 2 byte(s) (lsls r0, r0, 3) = wx c000
Here we simply logical shift left 3 times therefore 250 x 2 = 500, 500 x 2 = 1000, 1000 x 2 = 2000.
Let's verify.
:> pd 1 @ 0x00000332 │ 0x00000332 c000 lsls r0, r0, 3
All we have to do now is exit and convert our .elf to .uf2!
./elf2uf2/elf2uf2 0x03_char.elf 0x03_char.uf2
Plug in the Pico and make sure you hold down BOOTSEL or use the setup I provided in the part 2.
cp 0x03_char.uf2 /Volumes/RPI-RP2
Let's screen it!
screen /dev/tty.usbmodem0000000000001
AHH yea!
y y y y y y
We see 'y' printed out every 2 seconds!
In our next lesson we will discuss the int data type.