Part 15 - Debugging ADD
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
Let’s review our ADD example below:
Again we see that we move decimal 67 into r1 and decimal 53 into r2. We then add r1 and r2 and put the result into r0.
Let’s compile:
as -o add.o add.s
ld -o add add.o
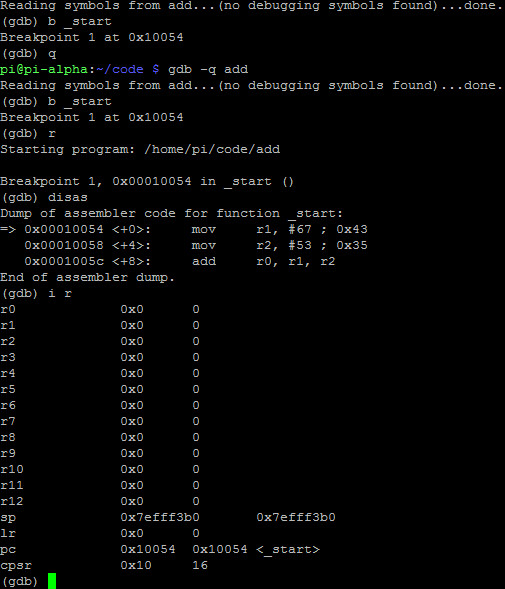
Let’s bring into GDB to debug:
gdb -q add
We can see that when we b _start, break on start and r, run we see the disassembly. If you do an i r we see the info registers where we notice our cpsr is 0x10.
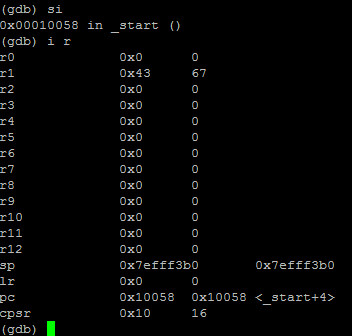
As we step again and info registers:
We notice 0x43 hex or 67 decimal into r1. We also notice that the flags are unchanged (cpsr 0x10).
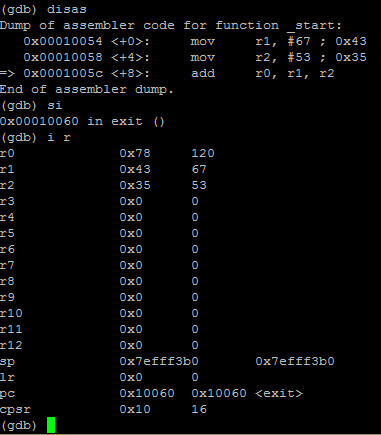
Let’s step again and info registers:
We can see r0 now holds 0x78 hex or 120 decimal. We successfully saw the add instruction in place and we again notice that the flags register (cpsr) remains unchanged by this operation.
Next week we will dive into Hacking ADD.