Part 14 - ADD
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
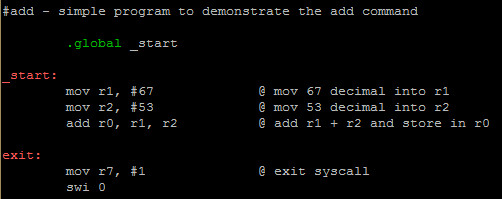
In ARM Assembly, we have three instructions that handle addition, the first being ADD, the second ADC (Add With Carry) and the final ADDS (Set Flag). This week we will focus on ADD.
Let’s look at an example to illustrate:
Here we see that we move decimal 67 into r1 and decimal 53 into r2. We then add r1 and r2 and put the result into r0.
"So what the heck is all that and why should I care?"
This series is going to be unlike any other in it's class. The goal is to take small pieces of code and see exactly what it does. If you are going to understand how to reverse a binary or malware of any kind, it is critical that you understand the basics. Learning ARM Assembly basics will help you when reversing an iPhone or Android. This tutorial series is going to work to take extremely small bites of code and talk about:
1)The Code: (Here) we speak briefly about what the code does.
2)The Debug: We break down the binary in the GDB Debugger and step though each instruction and see what specifically it does to program flow, register values and flags.
3)The Hack: We hack a piece of the code to make it do whatever WE want!
This approach will allow you to spend just a few minutes each week to get a good grasp on what is going on behind the scenes.
Next week we will dive into Debugging ADD.