Part 33 – Debugging Double Variables
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
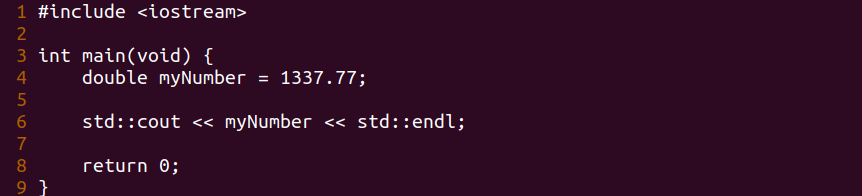
Let’s review our code.
int main(void) {
double myNumber = 1337.77;
std::cout << myNumber << std::endl;
return 0;
}
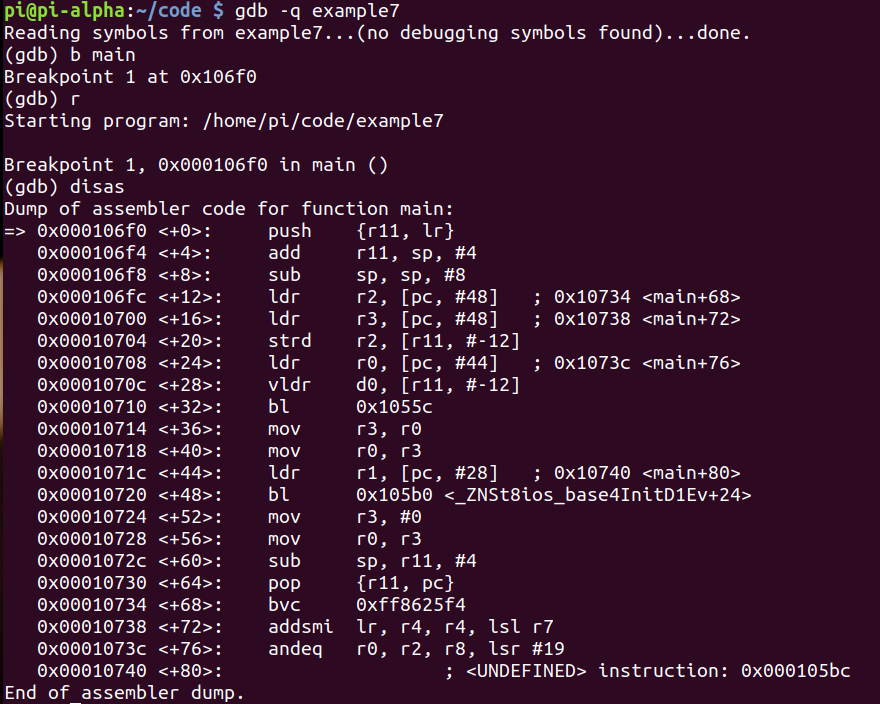
Let’s debug!
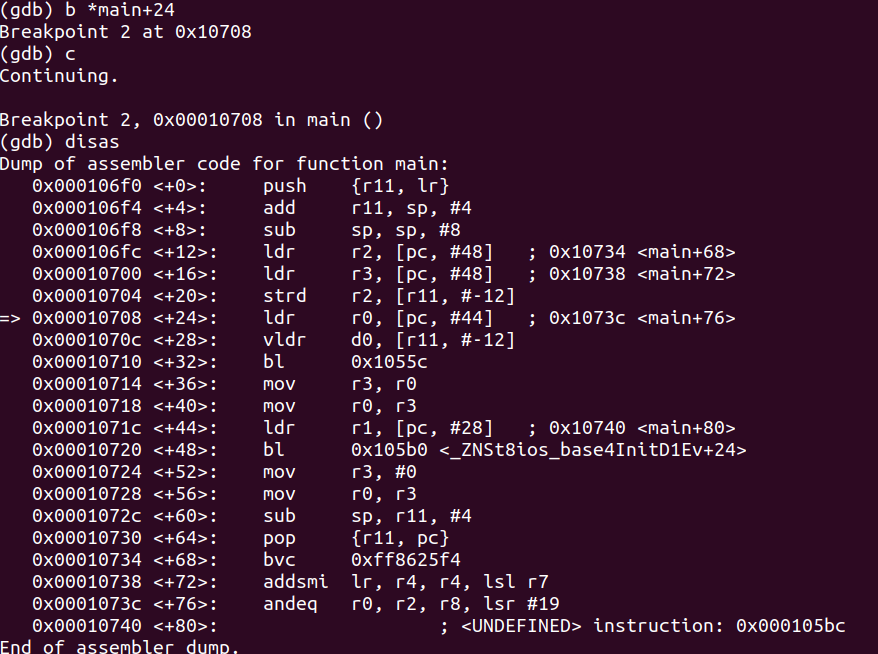
Let’s set a breakpoint at main+24 and continue.
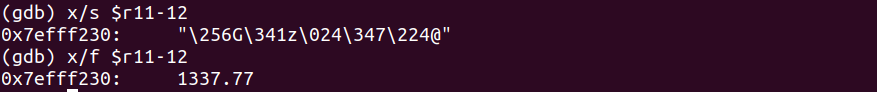
We see the strd r2, [r11, #-12] and we have to fully understand that this means we are storing the value at the offset of -12 from register r11 into r2. Let’s now examine what exactly resides there.
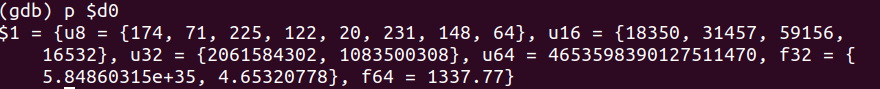
Voila! We see 1337.77 at that offset location or specifically stored into 0x7efff230 in memory.
Let’s step into twice which executes the vldr d0, [r11, #-12] as we understand that 1337.77 will now be loaded into the double precision math co-processor d0 register. Let’s now print the value at that location below.
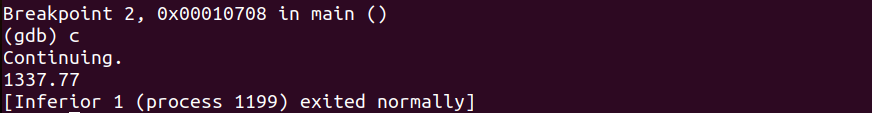
Finally let’s continue and watch the value echo to the terminal. This completes our cout c++ function.
Next week we will dive into Hacking Double Variables.