Part 43 - Hacking Pointers!
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
We are at the end of the road. This is the final video in the x64 series. The final topic is that of pointers.
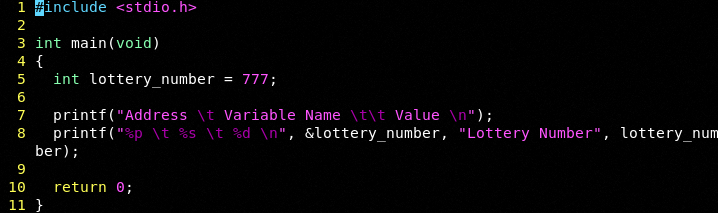
What are pointers? Let us start with an example.
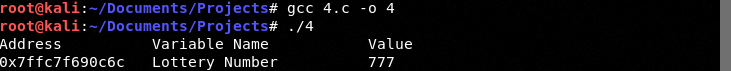
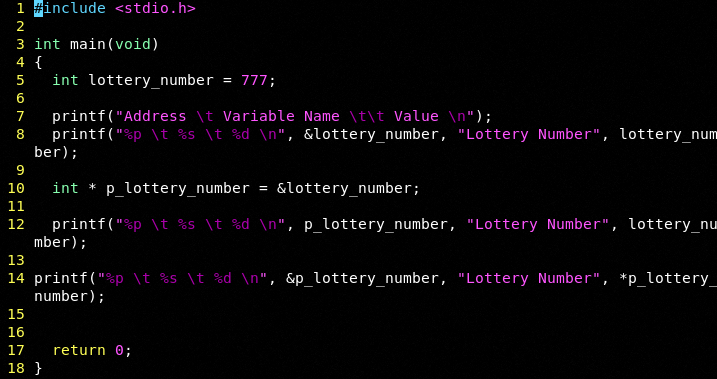
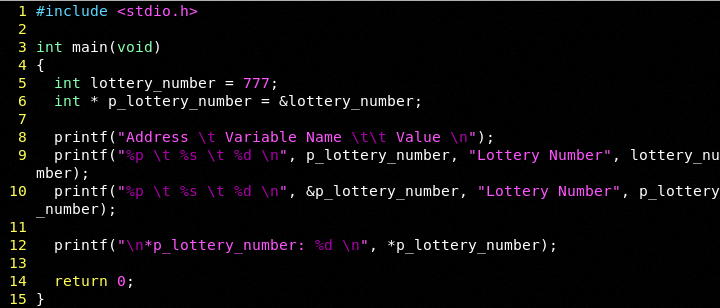
A pointer is nothing more than a memory address. When we compile we will clearly see where lottery_number lives in mapped memory (this is a running example unlike our unmapped Radare examples).
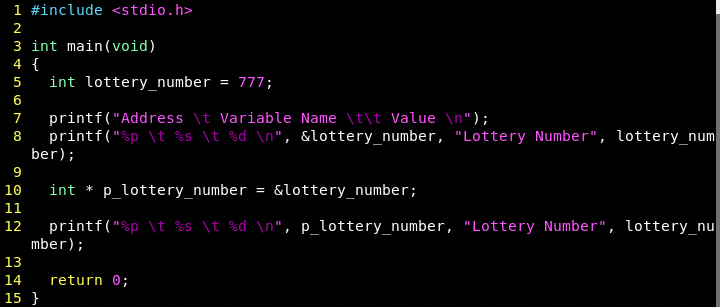
Let's add a true pointer to the example:
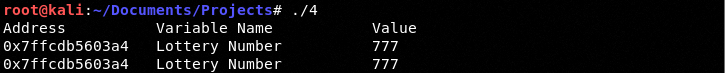
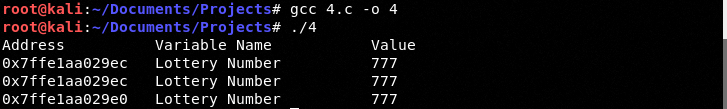
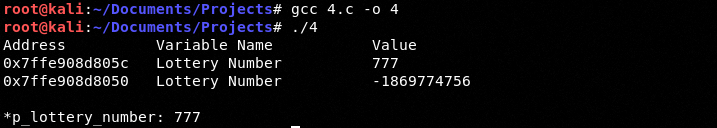
We see the same value:
Let us experiment more:
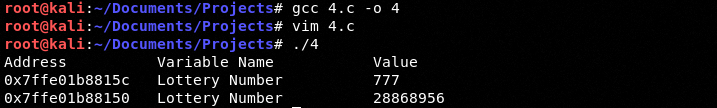
We see the pointer address point to a new address:
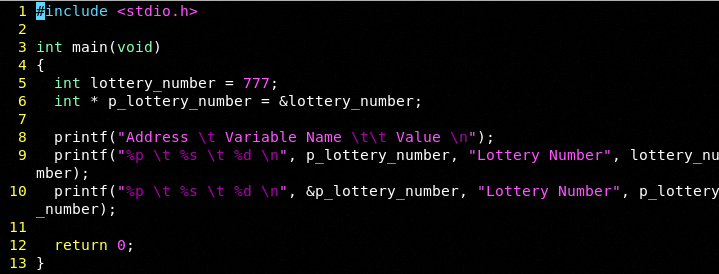
Remember pointers are memory addresses of other variables. Let's look at it another way:
Let us compile:
We deference by doing the following:
Then we compile:
We can see the deference pointer is equal to 777.
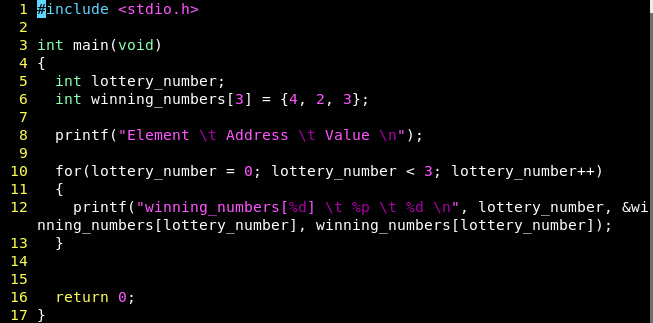
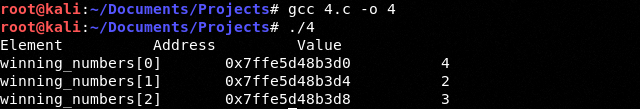
We can see the example with an array:
Let's debug:
Then we disassemble:
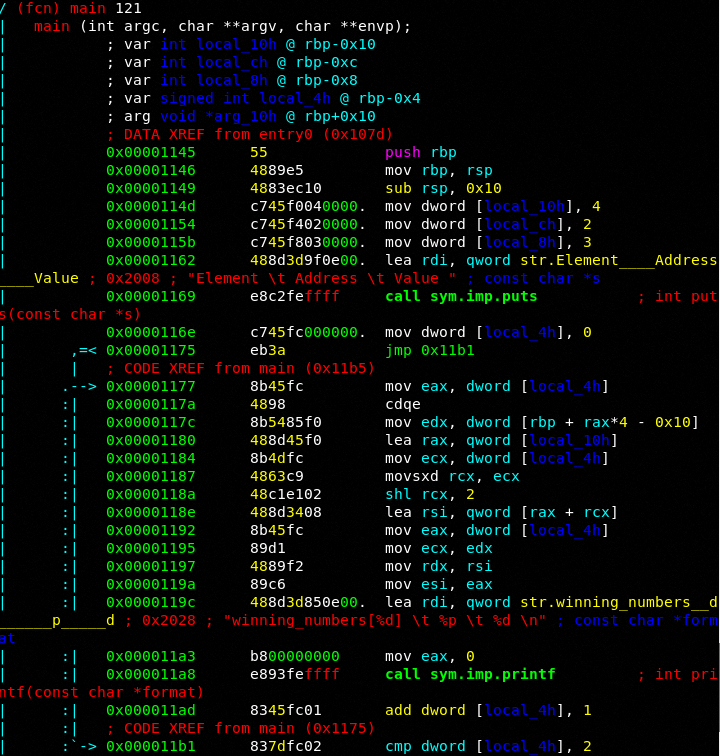
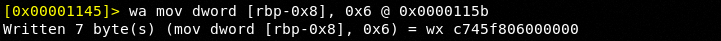
Let's hack!
Let's re-examine the binary:
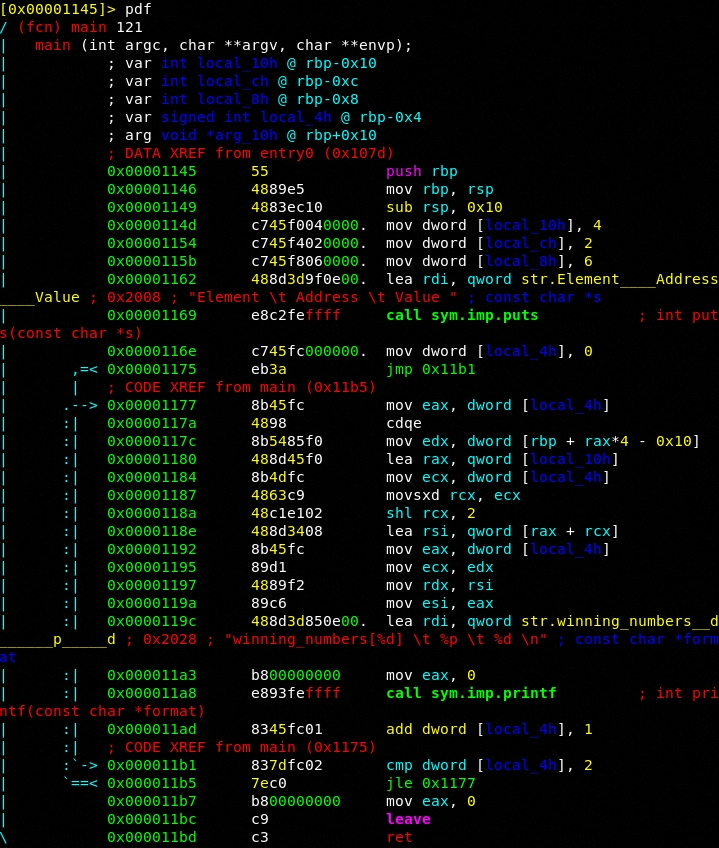
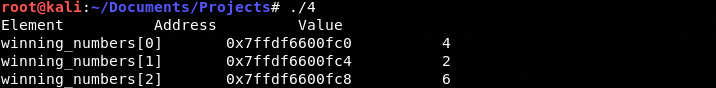
We can see we hacked the value of 3 with 6.
We can see we have made the successful hack.
I hope over the years through the literal hundreds of x86, ARM and x64 tutorials you have a basic knowledge of how to do GOOD to protect critical infrastructures from malicious hands by understanding how the enemy works. Go and do GOOD work!