Part 26 - ASM Debugging 2 [Moving Data Between Registers]
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
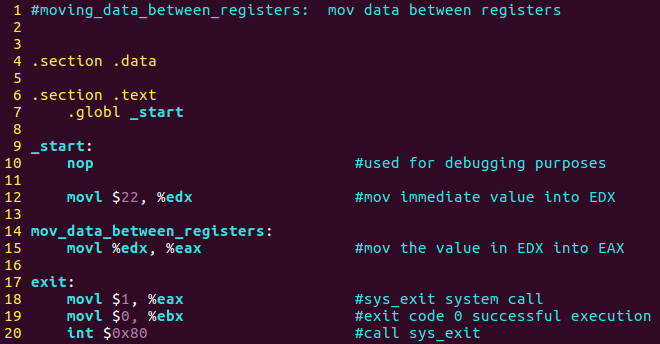
Let’s debug the second program below:
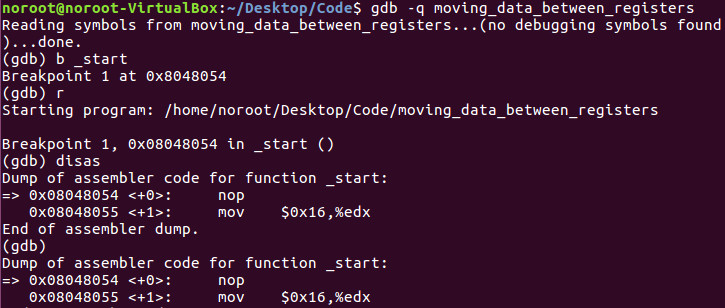
Lets fire up GDB and break on _start, run the binary and disas:
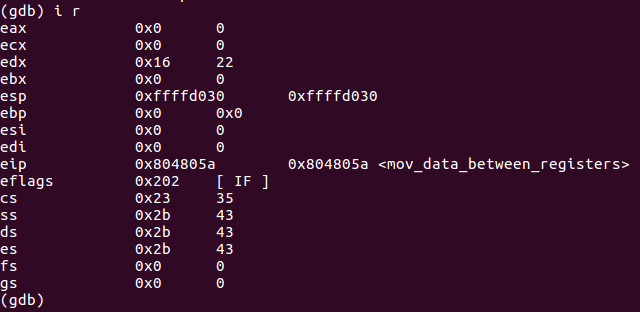
Now lets si twice and i r:
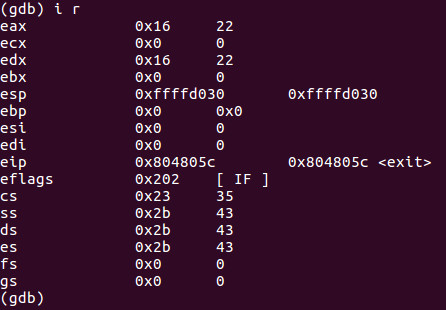
As we can see the value of 0x16 or 22 decimal did move into EDX successfully. Now lets si again.
As you can see we have successfully moved EDX into EAX.
I look forward to seeing you all next week when we dive into hacking our second assembly program!