Part 24 - ASM Hacking 1 [Moving Immediate Data]
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
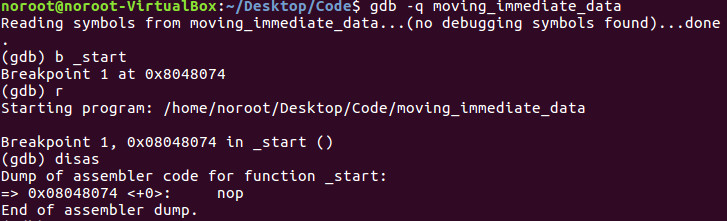
Let’s begin by loading the binary into GDB.
To load into GDB type:
gdb -q moving_immediate_data
Let’s first set a breakpoint on start by typing b _start.
We can then run the program by typing r.
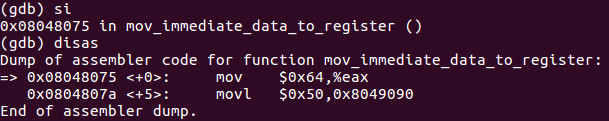
To then begin disassembly, we simply type disas.
We coded a nop which means no operation or 0x90 from an OPCODE perspective for proper debugging purposes which the breakpoint properly hit. This is good practice when creating assembly programs.
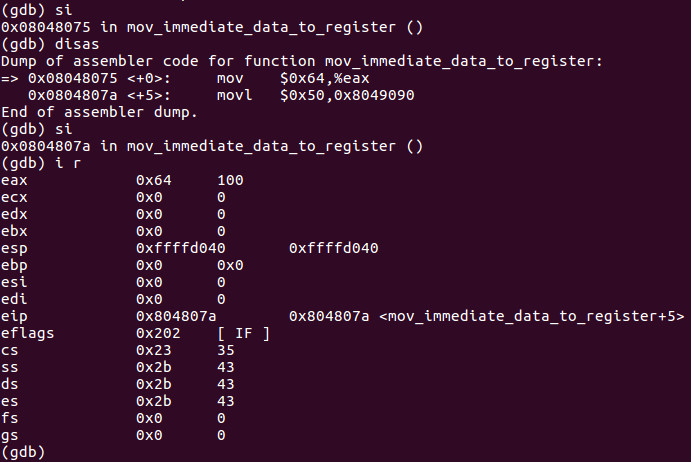
Lets have some fun! At this point lets si once and do an i r to see that 0x64 has in fact been moved into EAX.
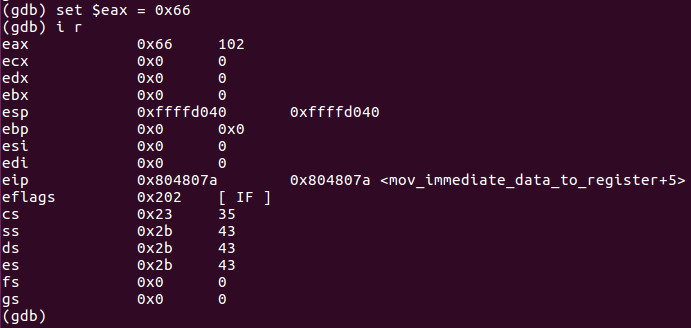
We can see EAX has the value of 0x64 or 100 decimal. Lets HACK that value now by setting EAX to say something like 0x66 by typing set $eax = 0x66.
BAM! There we go! You can see the ULTIMATE power of assembly here! We just hacked the value from 0x64 to 0x66 or 100 to 102 decimal. This is a trivial example however you can clearly see when you learn to master these concepts you develop a greater power over the computer. With each program that we create, we will have a very simple lesson like this where we will hijack at least one portion of the code so we can not only see how the program is created and debugged but how we can manipulate it to whatever we want.
I look forward to seeing you all next week when we dive into creating our second assembly program!