Part 42 - Hacking Branches!
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
Let's take a look at some branching logic:
As we can plainly see we init an int to 1 and if the variable is equal to 1 the first if statement prints a response to standard output.
Let's compile:
Let's run:
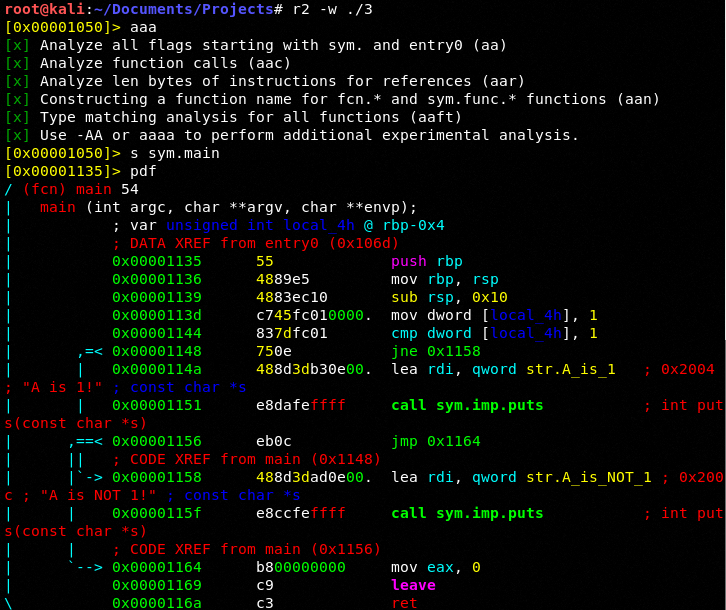
As we can logically see the first branch is taken. Let's take it into Radare and look around at the assembly:
We can see the branching logic with the aqua colored arrows. At 0x0000114a we see our first branch being loaded into rdi. Take note at 0x00001148 we see a jne 0x1158. At 0x00001158 we see our second branch being loaded into rdi.
The jne means jump if not equal. This means if what is being compared in 0x00001144 is not equal to 1 (we see 1 being compared to what is in local_4h which we know is pseudo code for what is actually in rbp-0x4. This should make sense as I went over this in detail last week if you are confused please revisit our last lesson.
To hack we simply make the jne statement to je which is jump if equal which we know the cmp or comparison is equal so it will now branch to "A is NOT 1!".
When we exit Radare we can see we have hacked the binary successfully:
Stay tuned!