Part 36 – Debugging SizeOf Operator
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
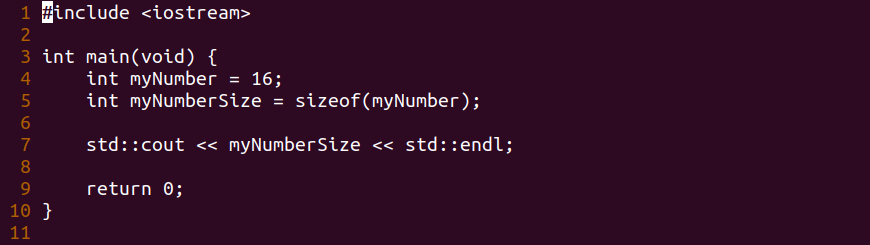
Let’s re-examine our code.
#include <iostream>
int main(void) {
int myNumber = 16;
int myNumberSize = sizeof(myNumber);
std::cout << myNumberSize << std::endl;
return 0;
}
Remember that we create a variable myNumber = 16 to which we create another variable myNumberSize which holds the value of the size of myNumber. We see that when we execute our code it shows 4 therefore we see that the SizeOf operator indicates an integer is 4 bytes wide.
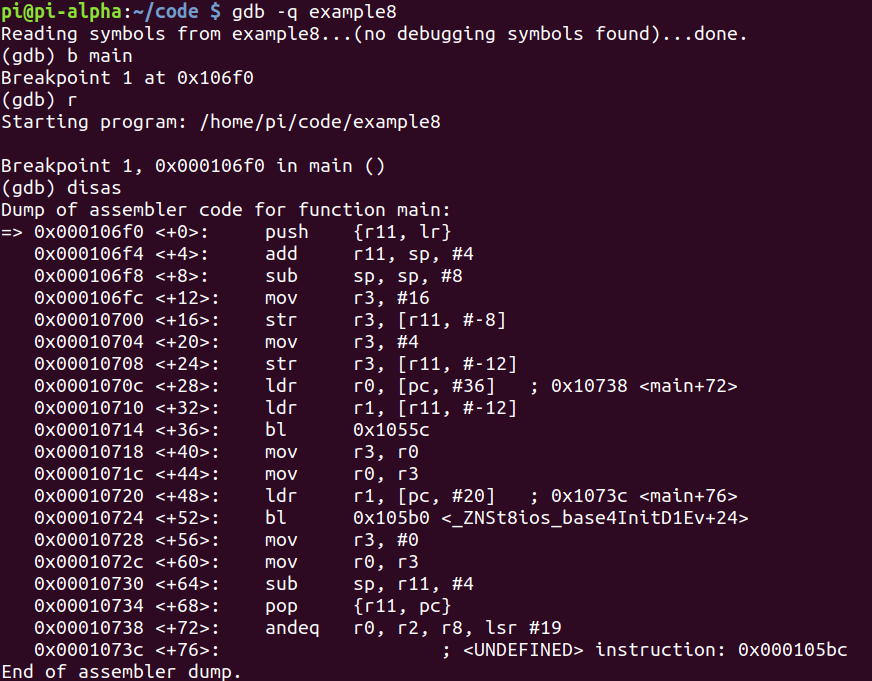
Let’s debug and break on main.
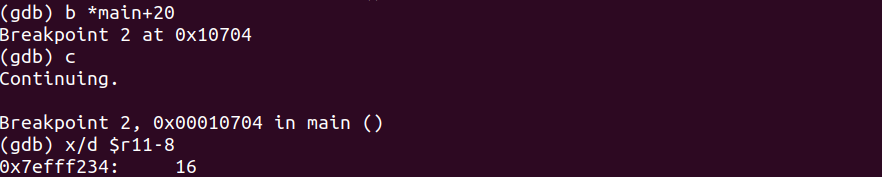
Let’s break on main+20 as we can see the value of 4 being moved into r3.
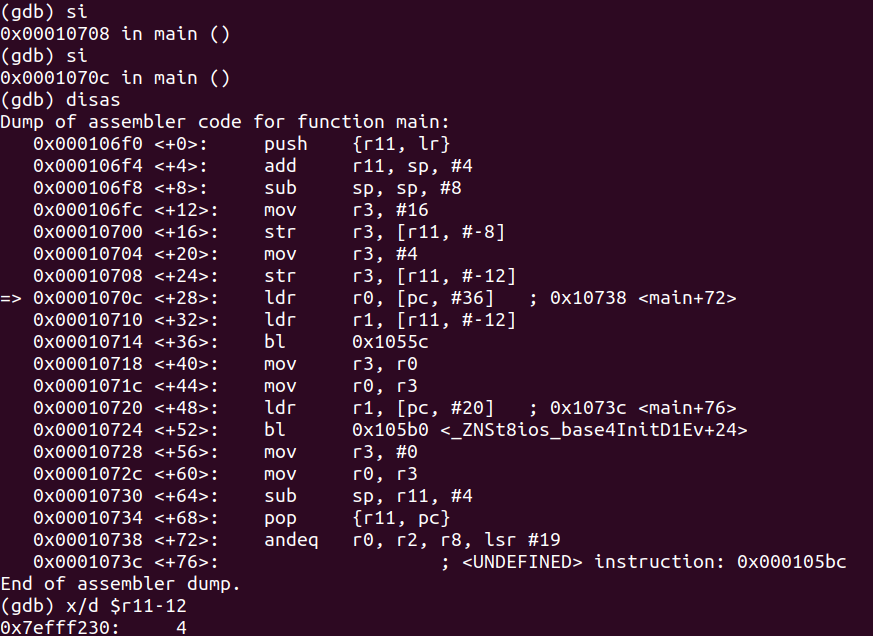
Let’s examine what is going on at main+16 as we can see that we are storing into the value of $r11-8 that which exists in r3 which in our case is 16. This makes sense as when we examine our original code the value of myNumber was in fact 16. We can see this here when we examine the value inside $r11-8.
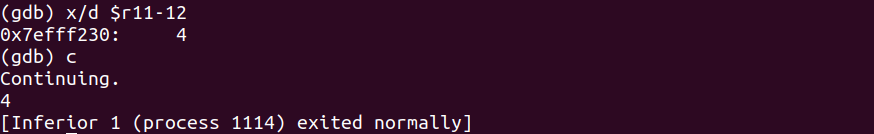
As we can see above the value inside $r11-12 is 4 as that represents the value that SizeOf is returning as the integer 16 is in fact 4 bytes wide.
Finally when we continue execution we in fact see the value 4 echoed to the terminal.
Next week we will dive into Hacking SizeOf Operator.