Part 18 – Debugging Constants
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
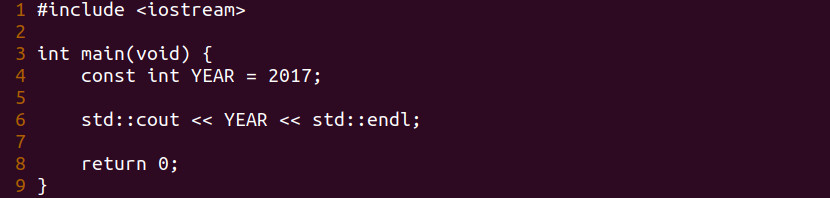
Let’s review last week’s code.
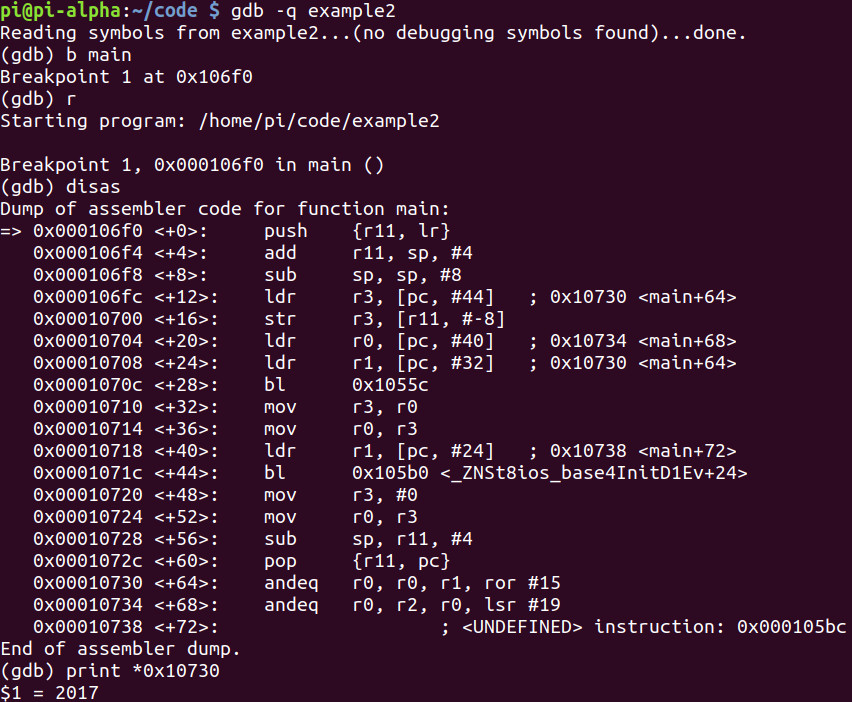
Let’s debug!
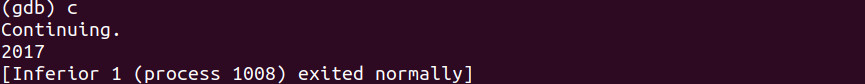
As we can see the value in the memory address 0x10730 is equal to 2017. Let’s continue and watch the value print to the standard output (terminal) as it did last week when we ran it.
We can see very clearly that we move the value from memory into r1 and then we branch to our cout function to print to the terminal. At this stage you should feel a little more comfortable with understanding what the assembly is doing above.
Next week we will dive into Hacking Constants.