Part 21 – Debugging Character Variables
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
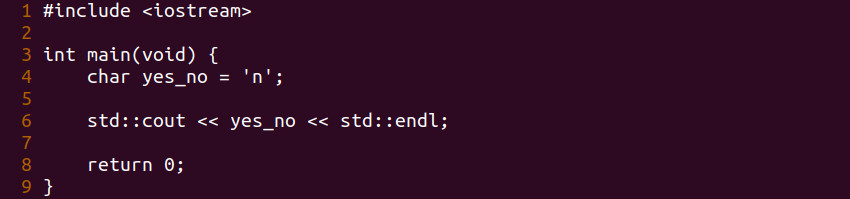
Let’s review our code.
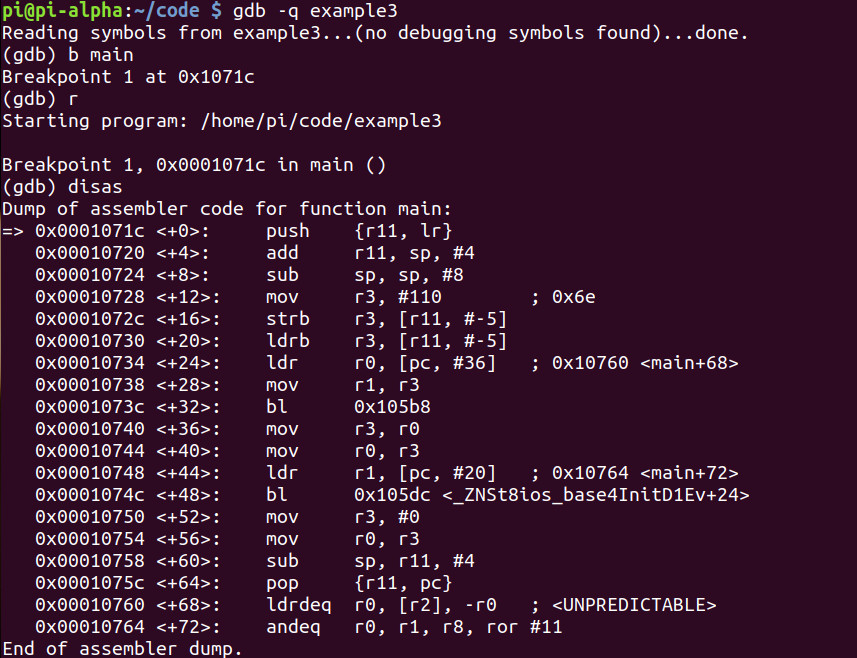
Let’s debug!
Woah! This is confusing. I don’t see any clear memory addresses being loaded into a register to manipulate the data.
Let’s keep in mind that we are dealing with a single byte character variable.
If you remember from last week each character translates down to an ASCII code in hex which the processor understands. The value of n is 0x6e hex or 110 decimal. You can review any ASCII table to see where we derived this value.
We do see 0x6e at main+12 which is the character ‘n’.
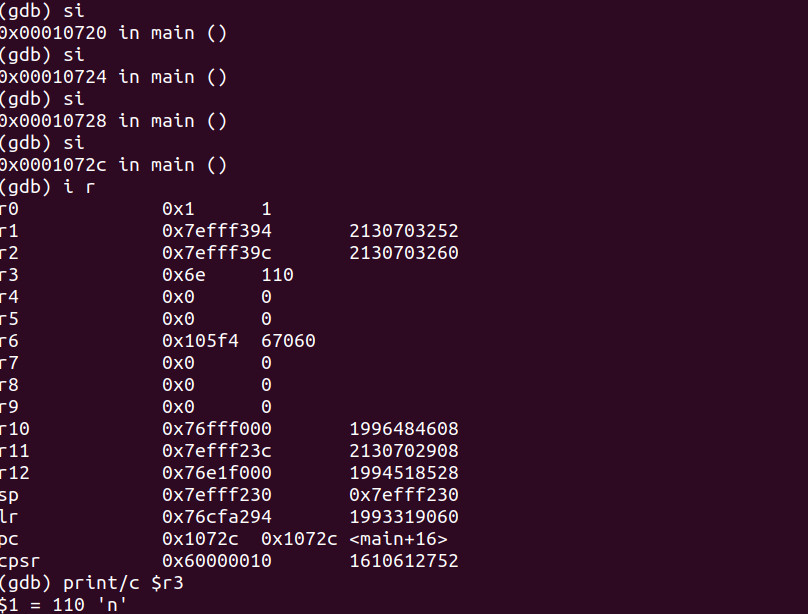
If we step into a few times we notice the value has been placed into r3. When we print the value in r3 we now see our ‘n’ character.
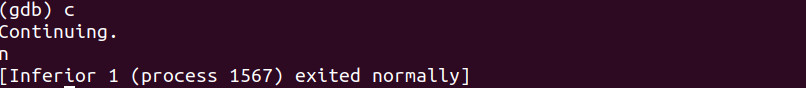
Let’s continue.
We now see the ‘n’ printed to the standard output as expected.
It is important that you understand this process and understand that each character translates into an ASCII value to which the processor loads directly into a respective register. Our previous experience we have seen a string loaded directly into a memory location and this is not the case here.
Next week we will dive into Hacking Character Variables.