Part 38 - ASM Debugging 6 [CMOV Instructions]
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
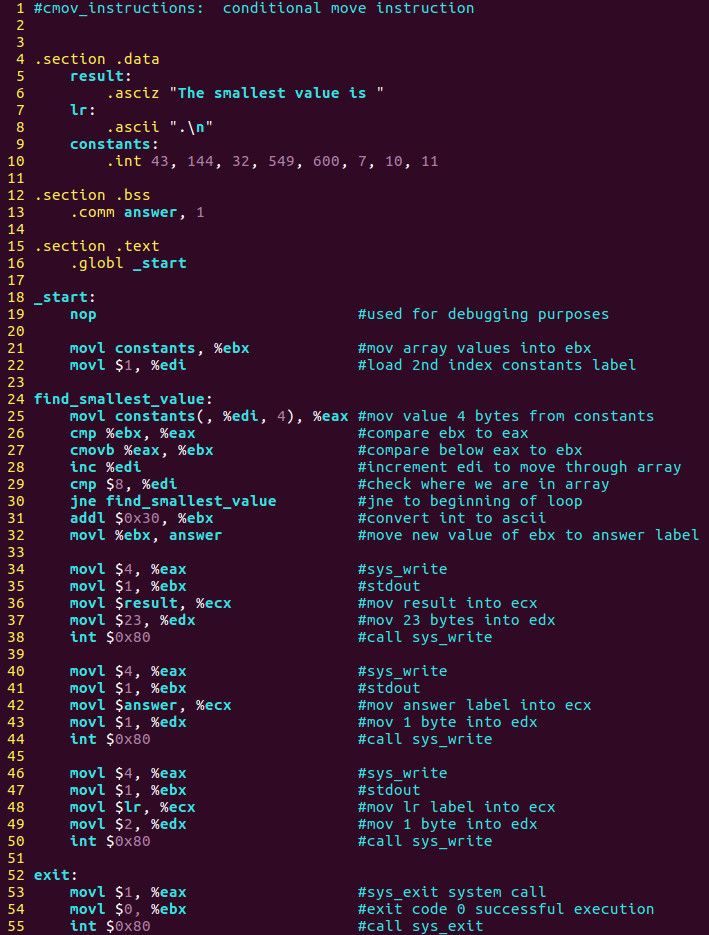
Lets re-examine some source code.
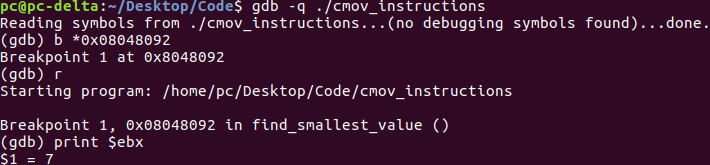
Lets break on 0x08048092 which is line 31. Lets do a r to run and then type print $ebx. We can see the value of 7.
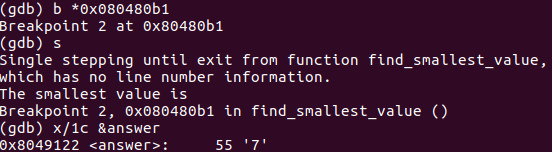
Ok now lets break on 0x080480b1 which is line 46. Remember when we are examining the value of answer, it has been converted to its ascii printable equivalent so in order to see the value of ‘7’ you would type x/1c &answer.
I look forward to seeing you all next week when we dive into hacking our sixth assembly program!