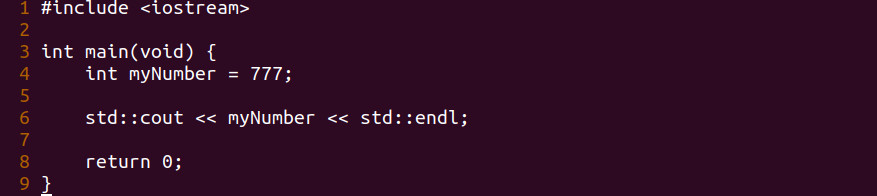
Part 27 – Debugging Integer Variables
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
Let’s review our code. I again want to include the below information from last week’s lesson to emphasize what is going on regarding integers.
A 32-bit register can store 2^32 different values. The range of integer values that can be stored in 32 bits depends on the integer representation used. With the two most common representations, the range is 0 through 4,294,967,295 (2^32 − 1) for representation as an (unsigned) binary number, and −2,147,483,648 (−2^31) through 2,147,483,647 (2^31 − 1) for representation as two's complement.
Keep in mind with 32-bit memory addresses you can directly access a maximum of 4 GB of byte-addressable memory.
Let’s debug!
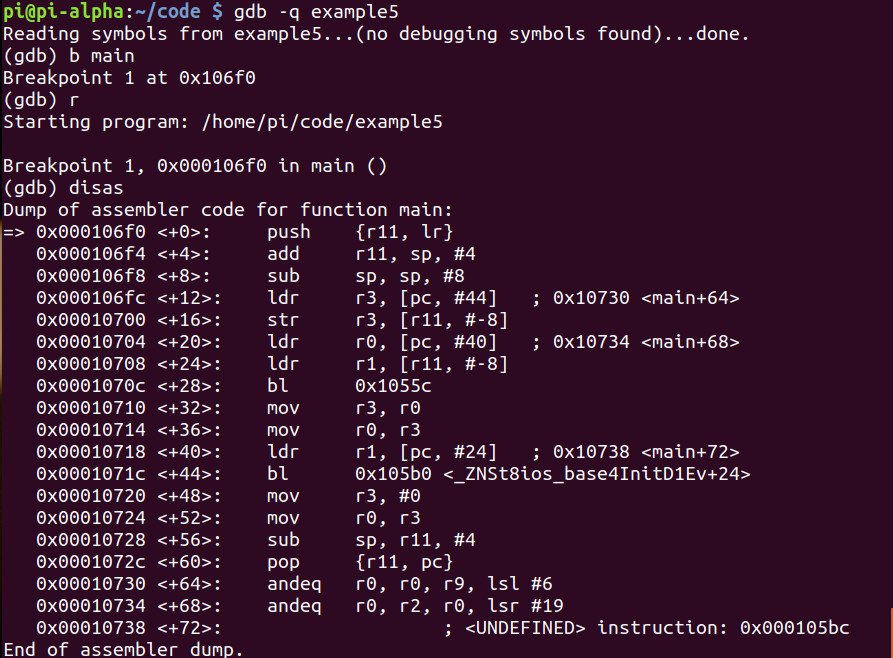
We see at main+12 the address at 0x10730 loading data into r3. Let’s take a closer look.
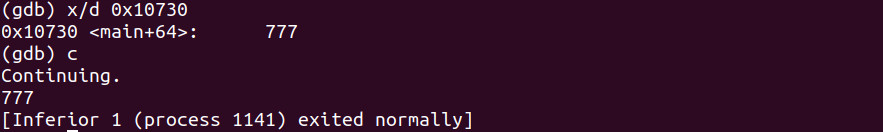
When we examine the data inside 0x10730 we clearly see the integer 777 present. When we continue we see 777 echoed back to the terminal which makes sense as we utilized the cout function within c++.#linux #arm #asm #cplusplus #reverseengineering
Next week we will dive into Hacking Integer Variables.