Part 17 - ADDS
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
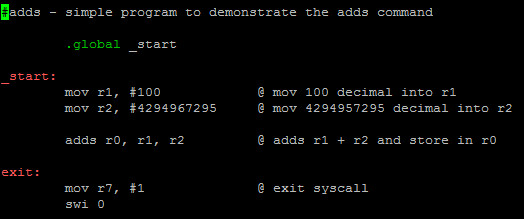
ADDS is the same as ADD except it sets the flags accordingly in the CPSR.
Let’s look at an example to illustrate:
We add 100 decimal into r1, 4,294,967,295 into r2. We then add r1 and r2 and place in r0.
We see adds which sets the flags in the CPSR. We have to remember when we debug in GDB, the value of the CPSR is in hex. In order to see what flags are set, we must convert the hex to binary. This will make sense as we start to debug and hack this example in the coming tutorials.
You can compile the above by:
as -o adc.o adc.s ld -o adc adc.o
We need to remember that bits 31, 20, 29 and 28 in the CPSR indicate the following:
bit 31 - N = Negative Flag
bit 30 - Z = Zero Flag
bit 29 - C = Carry Flag
bit 28 - V = Overflow Flag
Therefore if the value in binary was 0110 of bit 31, 30, 29 and 28 (NZCV) that would mean:
Negative Flag NOT Set
Zero Flag SET
Carry Flag SET
Overflow Flag NOT Set
It is critical that you compile, debug and hack each exercise in order to understand what is going on here.
Next week we will dive into Debugging ADDS.