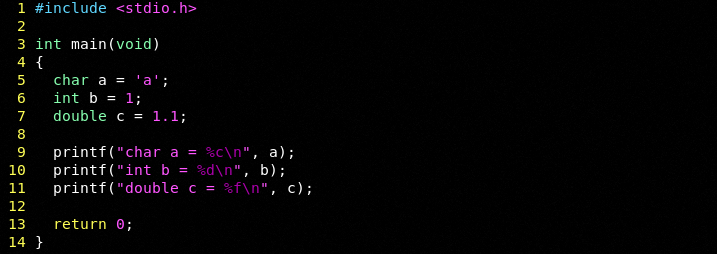Part 41 - Hacking Variables!
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
In C we have several data types to which we can create variables. I will use a few simple examples:
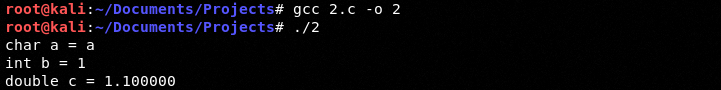
Let's compile and run:
Ok as we can see we have a character an integer and a double. These are some of the most basic data types in C to which we have created a series of variables as shown above.
Let us load the binary into Radare:
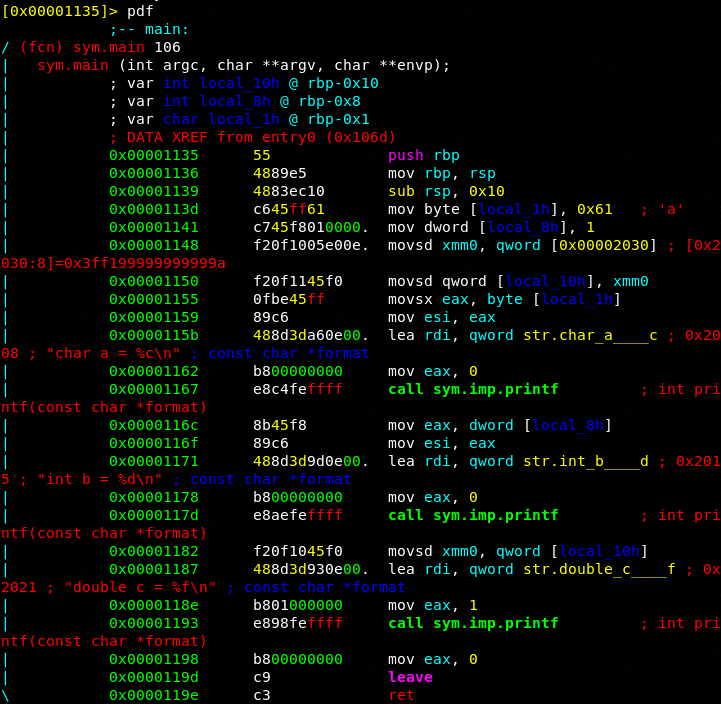
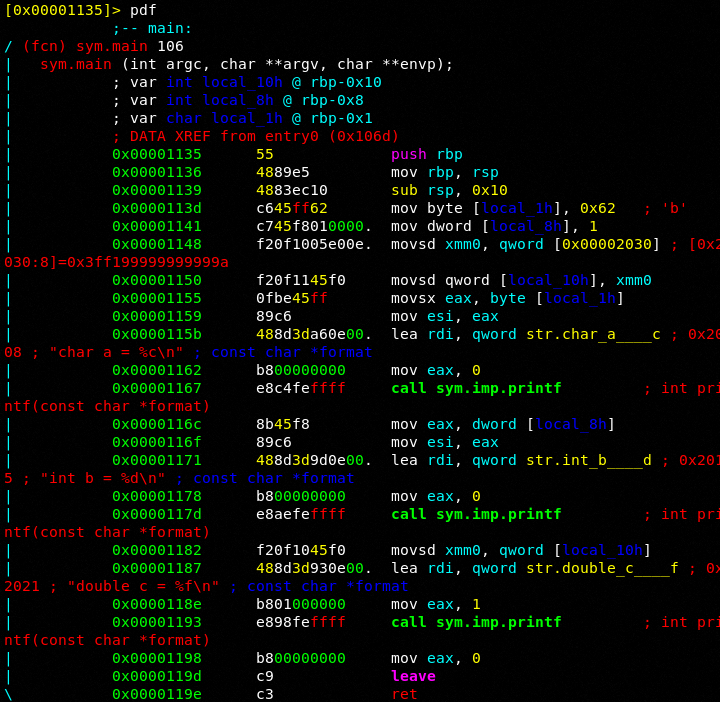
Let's disassemble at main:
Ok very simply we see 3 variable declarations defined up at the top in reverse order as they are local_1h which is our char a, local_8h which is our int b and local_10h which is our double c. You can also see the rbp base pointer allocating space for these variables. This is nice pseudo code that the debugger shows you up top.
Ok stay with me!
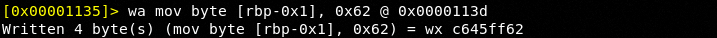
Within memory at 0x0000113d we see the instructions mov byte [local1_h], 0x61 which is in our ascii table a lowercase 'a'. We know that [local1_h] is not real code however what is going on under the hood is the fact that these variables are pushed onto the stack in reverse order as we can see above. Therefore, if we were to hack our code to something like mov byte [rbp-0x1], 0x62 what do you think might happen? Very simple, we know that in reality the code at the mapped memory address of 0x0000113d what is really going on is mov byte [rbp-0x1], 0x61. Quite simply what we have just done is hack our value of 'a' to 'b'. This should hopefully make sense to you.
Now let us re-examine our binary:
As we can clearly see at memory address 0x0000113d we in fact see 'b'. We have successfully hacked this portion.
We exit out of Radare and re-run the binary and we can see we have successfully hacked the value.
HOMEWORK TIME! I want you to with this knowledge now hack the int and the double. I want you to put your results in the comment sections below. It is VERY important that you type all of this out and actually explore the exercises so I am looking forward to seeing your hacks in the comments!