Part 27 - ASM Hacking 2 [Moving Data Between Registers]
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
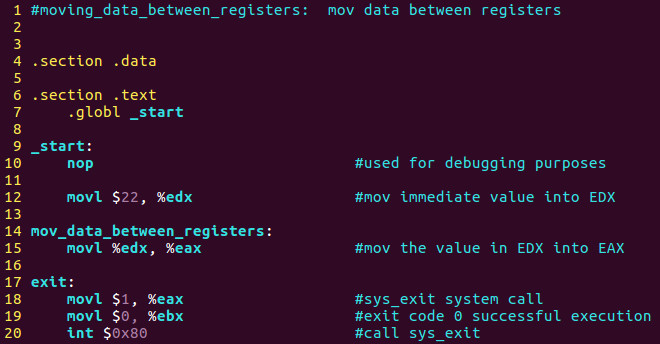
Let’s hack the second program below:
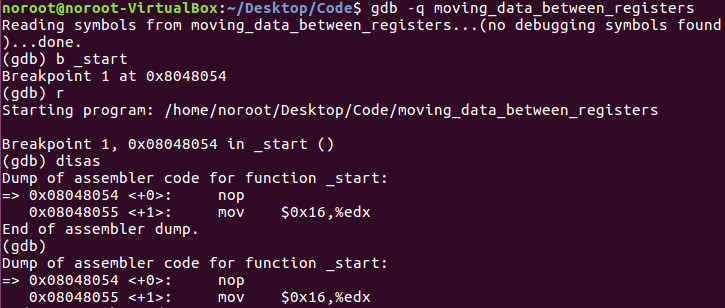
Lets fire up GDB and break on _start, run the binary and disas:
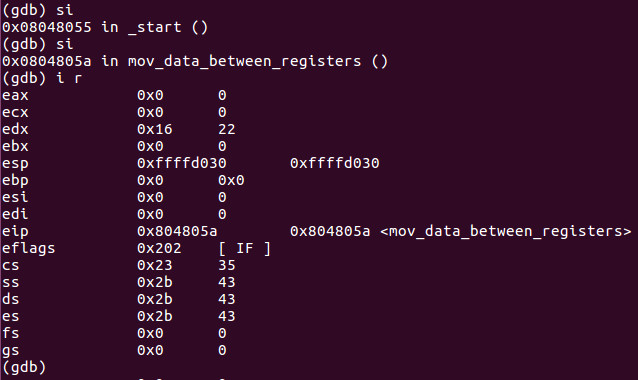
Now lets si twice and i r:
As we can see the value of 0x16 or 22 decimal did move into EDX successfully. This is what we did in the last lesson however here we are going to hack that value to something else.
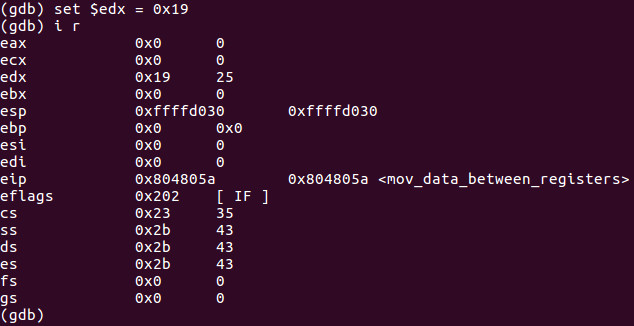
We can set $edx = 0x19 for example:
As you can see we easily hacked the value of EDX to 0x19 or 25 decimal.
Hopefully you see some very simple patterns now that we are diving into very simple assembly language programs. The key is to understand how to manipulate values and instructions so that you have complete control over the binary.
We are going to continue to move at a snails pace throughout the rest of this tutorial as my goal is to give everyone very small bite-size examples of how to understand x86 assembly.
I look forward to seeing you all next week when we dive into writing our third assembly program!