Part 16 - Hacking Hello World
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
Let’s review our code from two weeks ago.
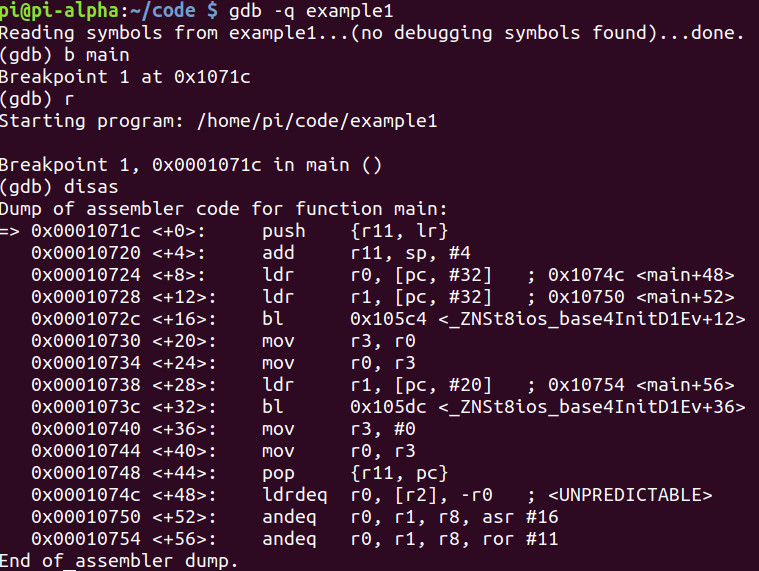
Let’s debug once again.
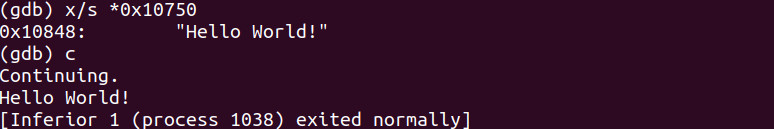
Let’s once again examine the contents of the string at memory address 0x10750 and continue through the execution of the program.
As you can see it holds the “Hello World!” string and when we continue through it echo’s back to the terminal as such.
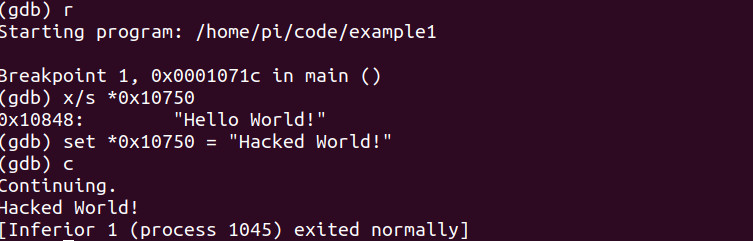
Let’s hack! Let’s now overwrite the value inside of the memory address with the string, “Hacked World!” and continue execution.
Woohoo! Our first hack! As you can see as you understand Assembly you have ABSOLUTE control over the entire binary no matter what language it is written in. In this very simple example we were able to hack the value inside the memory address of 0x10750 to which when executed it echoed, “Hacked World!” to the terminal or standard output.
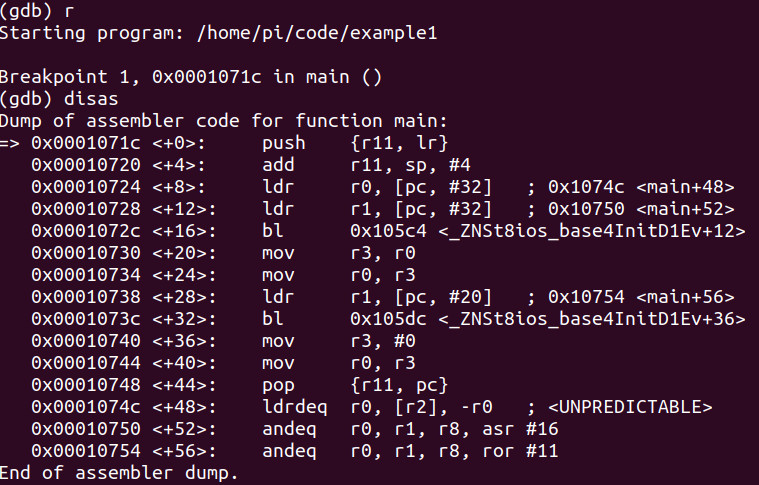
Let’s again run the binary and do a disassembly.
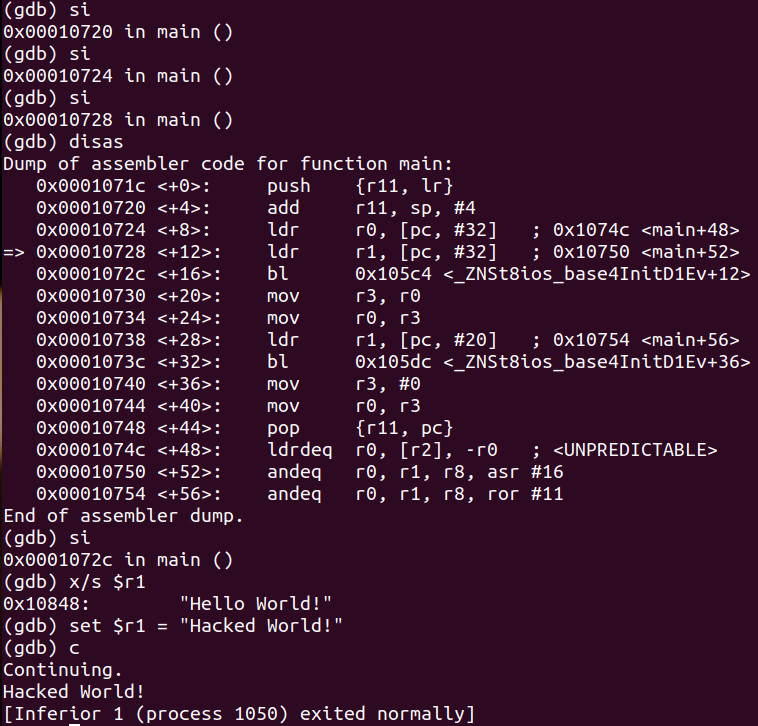
Let’s now do the same procedure however lets si 3x and examine the string inside of r1. We see that it contains, “Hello World!” as it has been successfully ldr (load from memory into the register) at main+12.
Let’s now set r1 to “Hacked World!” and continue execution. As you can see we now hacked it coming out of the register rather than in memory. You can clearly begin to see there are a number of ways to hack anything and here is a simple example of two such ways.
Reverse Engineering is all about understanding how a program executes and hijacking execution flow and changing values to suit our purpose! Today you took your first step into this amazing journey!
Next week we will dive into constants.