Part 25 – Hacking SUB
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
As stated, subtraction in ARM has four instructions which are SUB, SBC, RSB and RSC. We will start today with SUB.
Please keep in mind when you add the S suffix on the end of each such as SUBS, SBCS, RSBS, RSCS, it will affect the flags. We have spent enough time on flags in the prior lessons so that you should have a firm grasp on this now.
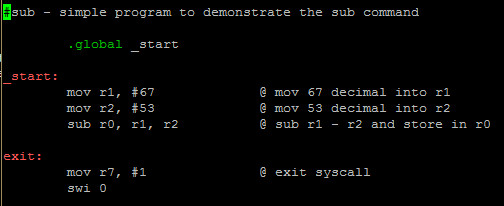
Let’s re-examine our example of SUB:
We simply take 67 decimal and move into r1 and 53 decimal and move into r2 and subtract r1 – r2 and put the result in r0.
Let’s hack.
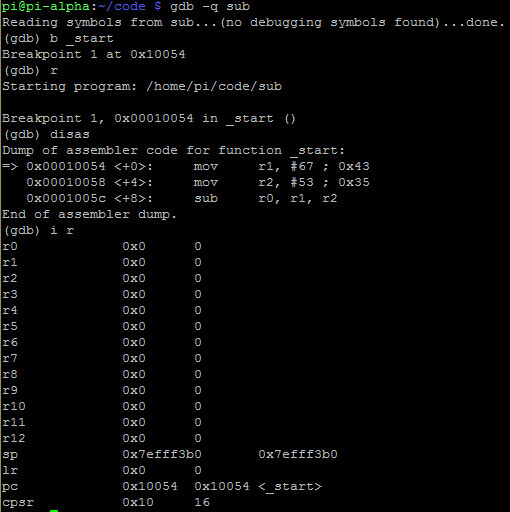
As we can see the registers are clear. Lets step through and see what the value of r0 becomes when we do a little hacking.
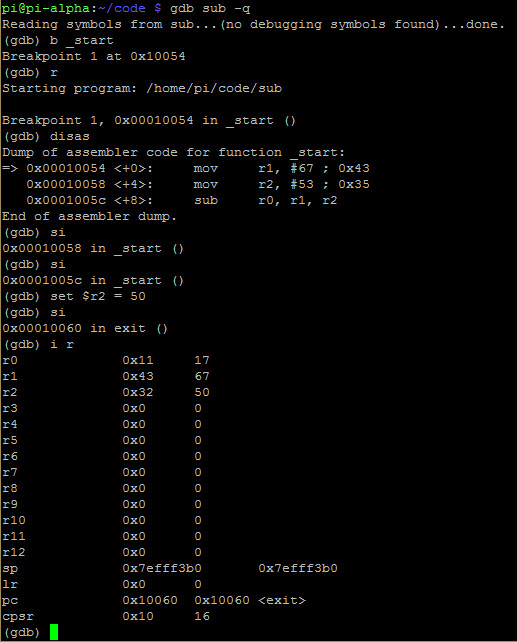
As you can see above r0 now has decimal 17 which works as expected as we hacked the value of r2 to decimal 50 instead of decimal 53.
I want to thank you all for taking this journey to learn ARM Assembly. This is the end of the series as I encourage you all to take what you have learned and continue to work through the ARM instruction set and continue your progress.
This tutorial’s purpose was to provide you a solid foundation in ARM Assembly and I believe we have done that. Thank you all and I look forward to seeing you all become future Reverse Engineers!