Part 49 – Hacking Post-Decrement Operator
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
Let's once again review our code.
#include <iostream>
int main(void) {
int myNumber = 16;
int myNewNumber = myNumber--;
std::cout << myNewNumber << std::endl;
std::cout << myNumber << std::endl;
return 0;
}
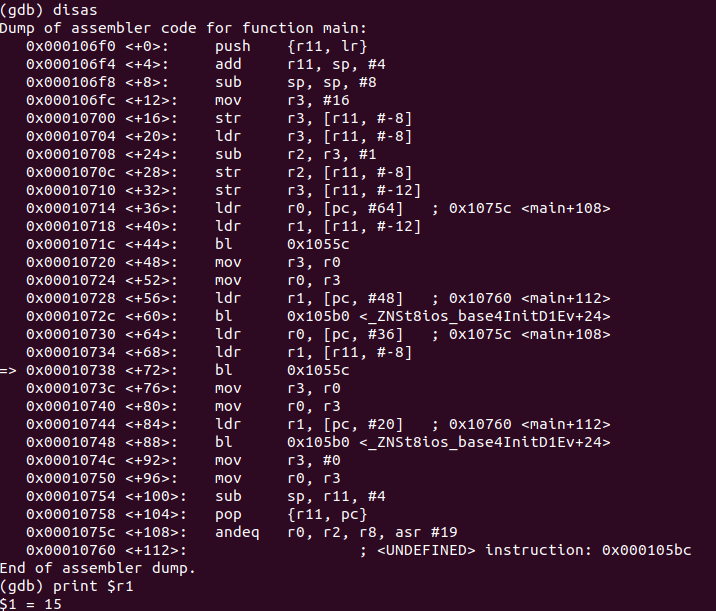
Let's review last week's debug.
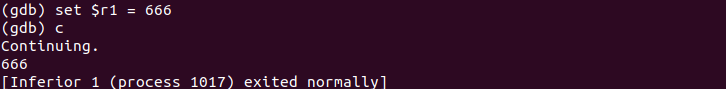
As we can see here the value in r1 at main+68 is 15. Let's hack!
Once again we have manipulated and changed program execution to our own bidding. With each of these bite-size lessons you continue to get a better grasp on the processor and how it interfaces with the binary.
I hope this series gives you a solid framework for understanding the ARM processor. This concludes the series. Thank you all for coming along on the journey!