Part 40 - Hacking Hello World!
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
Ok it is time we look at the most basic C program, debug it and hack it. If we are to have mastery we must create and destroy in a single-step so that we have mastery over the domain.
Let us fire up VIM and type out the following. We include our standard library and create a main function to which we use the library function of printf to echo a string of chars and since the type of main is int meaning integer we return 0.
Let us compile and see what happens when we run:
As we see like we did in our C++ example we see 'Hello World!' echoed successfully.
Let's debug in Radare:
This is simple, we use aaa to analyze the binary and seek to main with s sym.main.
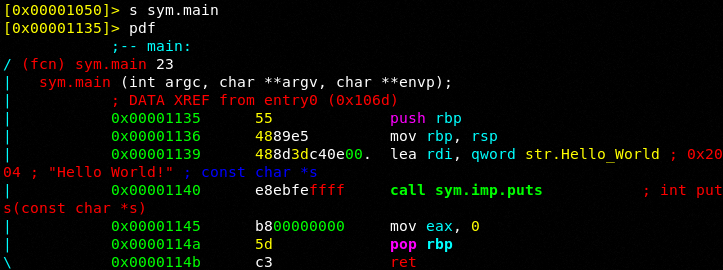
Let's look at the assembly and analyze:
Assembly! The definition of raw sexy!
I went over this in detail in the previous lessons on Assembly but let us review.
1)We push rbp which means we push the value currently in the base pointer onto the stack.
2)We lea rdi, qword str.Hello_World which means we load the effective address of the quad word of our string into the rdi register. So far should be simple for you to follow along.
3)We then call sym.imp.puts um wait! We used printf what the hell! Well our compiler optimizes our code and the compiler chose the puts function in the stdio library to echo the string to our terminal. Again easy enough.
4)We clean out eax and then pop the original value in the rbp register back into rbp. If you are confused by this review the earlier part of the series please.
We know our string 'Hello World!' lives at a pretty house in Arlington, VA at the address of 0x2004 well ok, it's not Arlington, VA but it is in mapped memory (since we are not technically debugging we are messing with mapped code meaning the same values on disk).
To confirm we see the value at 0x2004 is 'Hello World!' Let's hack that value to anything we want with the w command and write directly to that mapped memory address.
Let us re-examine who NOW lives in our Arlington, VA house!
Success! We hacked the value and when we exit our debugger we see:
We have successfully altered the binary.
This is alot to digest here. If you are stumped ask questions in the comments PLEASE! Do not continue as I am here to help. It is CRITICAL you understand these most basic things before we continue!