Part 15 - Debugging Hello World
For a complete table of contents of all the lessons please click below as it will give you a brief of each lesson in addition to the topics it will cover. https://github.com/mytechnotalent/Reverse-Engineering-Tutorial
Let’s review our code from last week.
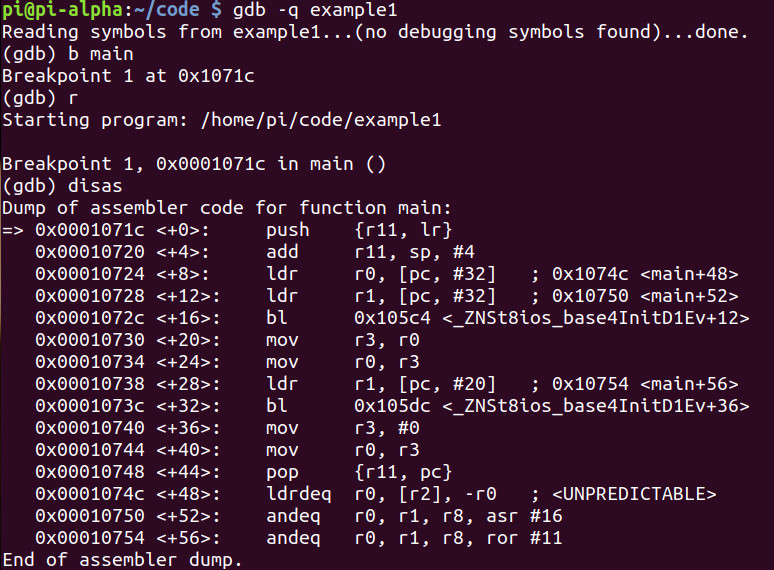
Let’s debug! Let’s fire up GDB which is the GNU Debugger to which we will break down the C++ binary and step through it line-by-line in ARM Assembly.
This is the ARM disassembly that we are seeing. No matter what language you program in, it ultimately will go down to this level.
This might be a bit scary to you if you did not take my prior course on ARM Assembly. If you need to do a refresher, please link back to that series.
You are probably asking yourself why we are not debugging with the original source code and seeing how it matches nicely to the assembly. The answer is when you are a professional Reverse Engineer, you do not get the luxury of seeing source code when you are reversing binaries.
This is a childishly simple example and we will continue through the series with very simple examples so that you can learn effective techniques. We are using a text-based debugger here so that you fully understand what is going on and to also get some training if you had to ever attach yourself to a running process inside a foreign machine you will know how to properly debug or hack.
I will focus SOLELY on this method rather than using a nice graphical debugger like IDA or the like so that you are able to manipulate at a very low-level.
We start with loading the link register into r11 and adding 4 to the stack pointer and then adding it to r11. This is simply a routine which will allow the binary to preserve the link register and setting up space on the stack.
We notice memory address 0x10750 being loaded from memory to the register r1. Let’s do a string examination and see what is located at that address.
Voila! We see our string. “Hello World!” located at that memory address.
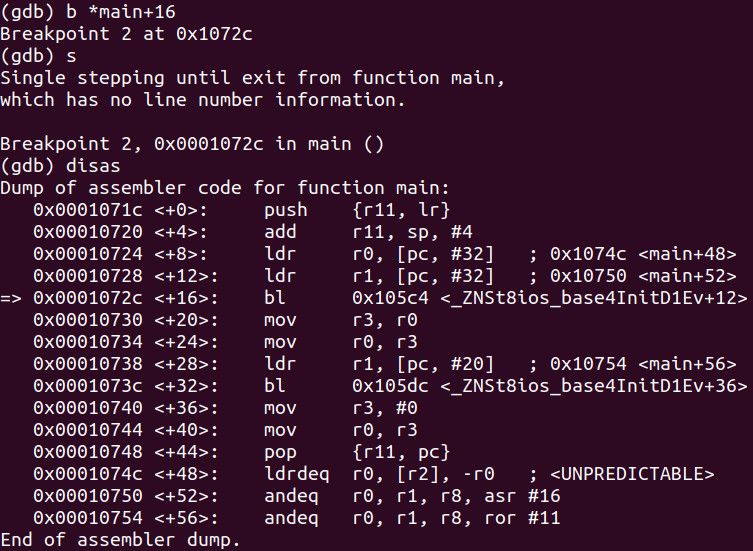
Let’s set a breakpoint at main+16.
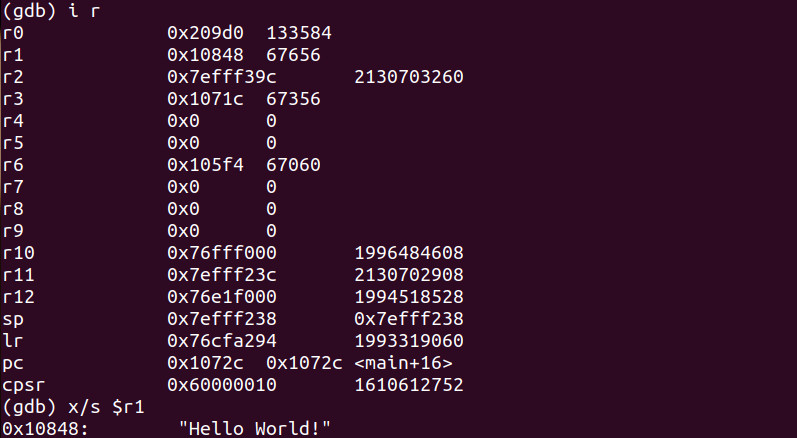
Let’s take a look at our register values.
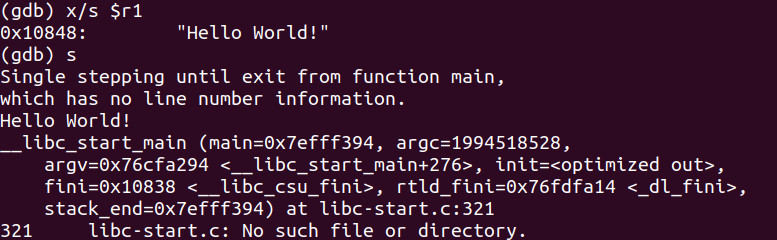
Let’s now take a look at what is inside the r1 register and then step through the binary.
We see the “Hello World!” string now residing inside of r1 which resides at memory address 0x10848. Finally let’s continue through the binary.
Understanding assembly and step-by-step debugging allows you to have complete and ultimate control over any binary! More complex binaries can cause you hours, days or weeks to truly Reverse Engineer however the techniques are the same just more time consuming.
Reverse Engineering is the most sophisticated form of analysis in advanced Computer Engineering. There are many tools that a professional Reverse Engineer uses however each of those tools have a usage and purpose however this technique is the most sophisticated and comprehensive.
Next week we will dive into Hacking Hello World.